The Illusion of Security: Why the Latest Linux Supply Chain Compromise Might Not Be as Bad as You Think
As news of a backdoor implanted in the latest versions of XZ Utils spreads like wildfire, the panic among Linux users is palpable. Red Hat and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) have sounded the alarm, warning about the supply chain compromise affecting Linux distributions. But is the situation really as dire as it seems?
Questioning the Hype
While the malicious code is said to allow unauthorized access, the actual extent of the threat remains unclear. Red Hat’s strong recommendation to halt the usage of Fedora Rawhide instances may be an overreaction. How often do such backdoors lead to real-world breaches, and are users justified in their fear?
The Case for Rational Response
Before rushing to downgrade XZ Utils and scouring for potential threats, it’s crucial to assess the practical implications of this compromise. How many users are truly at risk, and is the effort to revert to a previous version justified by the actual threat level?
Lessons from History
Supply chain compromises have indeed caused significant cyberattacks in the past, with SolarWinds and Kaseya VSA serving as stark reminders of the vulnerabilities in our digital infrastructure. However, each incident is unique, and knee-jerk reactions may not always be the most effective response.
Moving Forward
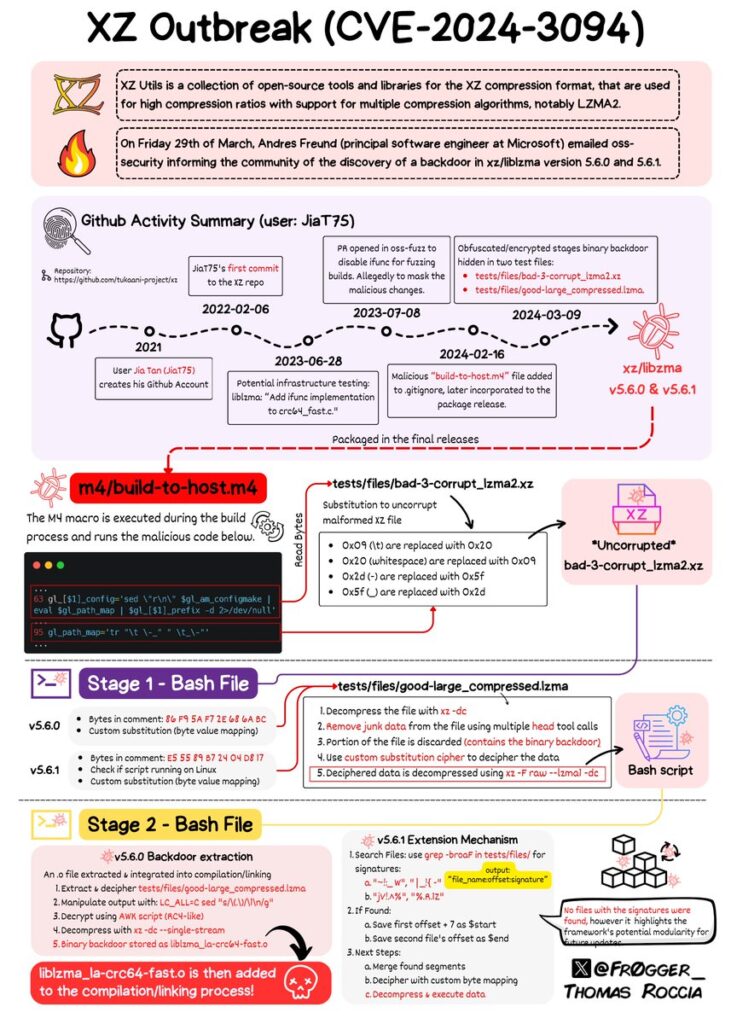
As the vulnerability is tracked under CVE-2024-3094, it’s essential to stay informed and vigilant. While CISA’s recommendations should not be dismissed outright, a balanced approach that considers the actual risk posed by the backdoor is crucial.
In conclusion, while the latest Linux supply chain compromise is undoubtedly concerning, it’s essential not to succumb to fearmongering. By critically evaluating the situation and responding rationally, users can navigate this challenge with resilience and confidence.