Understanding Linux File Permissions with umask
In the world of Linux, file permissions play a crucial role in ensuring the security and integrity of the system. One key aspect of file permissions that often goes unnoticed is the umask (Set File Mode Creation Mask) value. Let’s delve into what umask is all about and how it impacts file creation.
When a new file or directory is created in Linux, the default file mode permissions are typically set to 666 (rw-rw-rw). However, these permissions are not applied as is. They are actually masked or filtered by the umask value. For example, if the umask is set to 0022, the resulting permissions of a newly created file would be 644 (rw-r–r–).
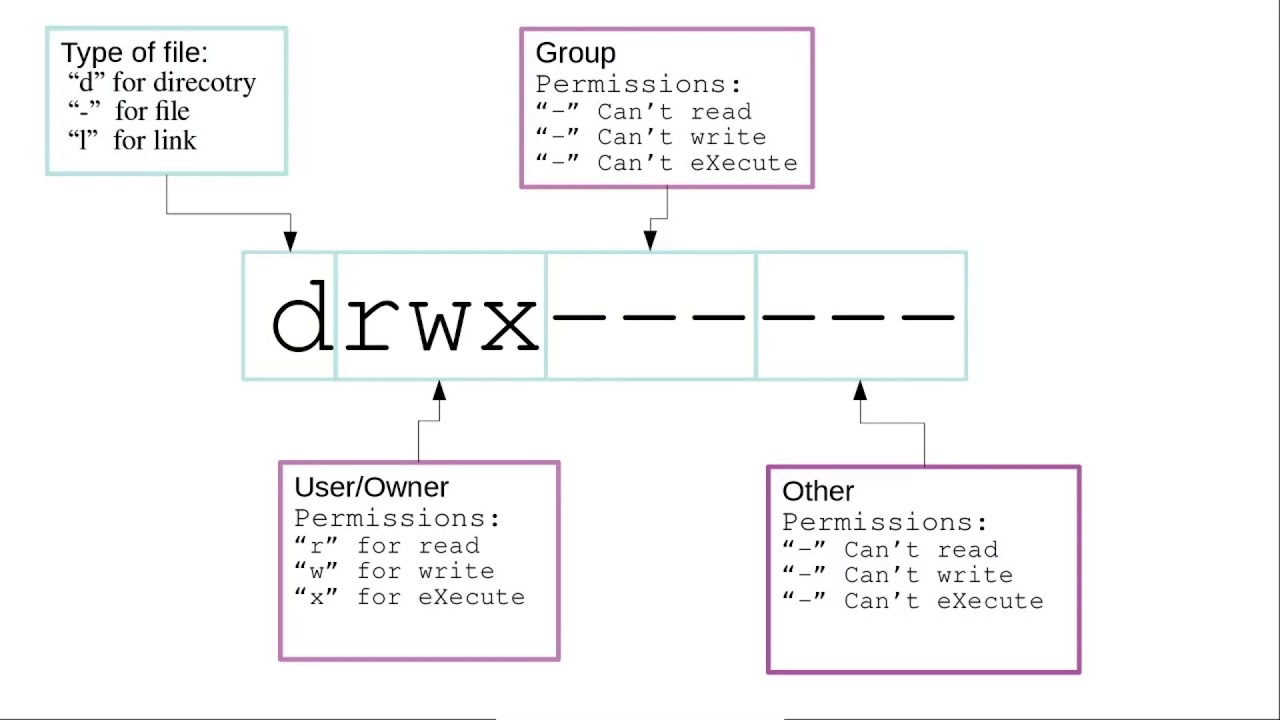
A visual representation of Linux file permissions
The umask value essentially acts as a system call that sets the file mode creation mask. It always succeeds and returns the previous value of the mask. Unlike the chmod syscall that affects specific files or directories, umask affects every file or directory created by the user.
In most Linux distributions, the umask values are configured in system-wide configuration files such as /etc/profile or /etc/bash.bashrc. These configurations define the default permissions for newly created files.
Moreover, depending on the shell environment used, umask can be either a dedicated binary or a built-in command of the shell. When the umask binary is used, the value can be read without altering it. However, for changing the umask value within the same process session, the built-in shell command is required.
Overall, understanding umask is essential for Linux users to manage file permissions effectively and maintain system security. Stay tuned for more insights into Linux security practices!
Follow us for more articles on:
- Linux
- Security
- Technology
- Infosec
- DevOps
See you in my next writeup ;-) You can follow me on Twitter for more updates.