The Growing Threat of Linux Malware Campaigns
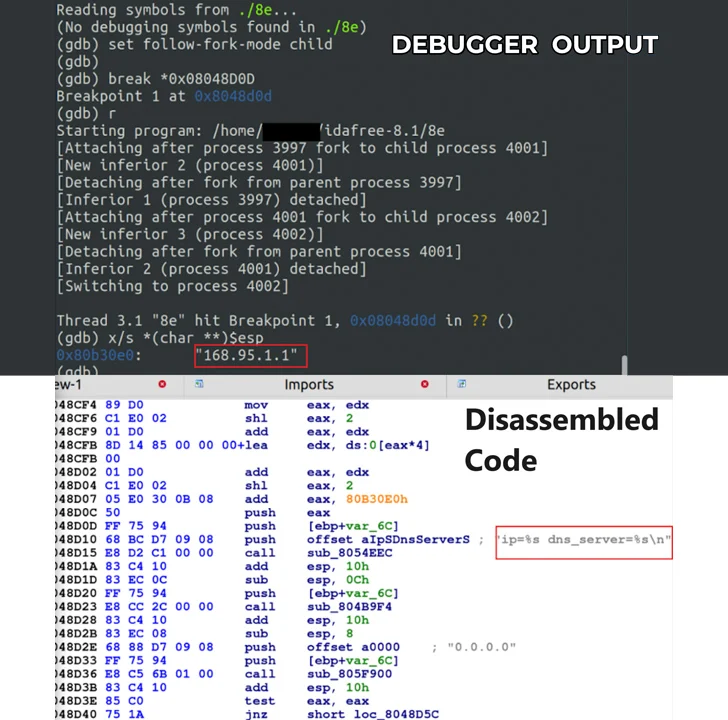
As a cybersecurity enthusiast, I am always on the lookout for the latest developments in the digital security landscape. This week, my attention was drawn to a concerning trend - a new Linux malware campaign targeting misconfigured servers running Apache Hadoop YARN, Docker, Confluence, and Redis. The campaign, which leverages previously unreported payloads, exploits common misconfigurations and takes advantage of a Confluence CVE to carry out remote code execution (RCE) attacks.
Targeting Misconfigured Servers
The discovery of this Linux malware campaign serves as a stark reminder of the importance of properly configuring and securing servers. In today’s interconnected world, where data is a valuable commodity, cybercriminals are constantly seeking ways to exploit vulnerabilities for their gain. By targeting servers running popular platforms like Apache Hadoop YARN, Docker, Confluence, and Redis, the attackers aim to infiltrate sensitive systems and carry out malicious activities.
Diversification of Ransomware Tactics
In addition to the Linux malware campaign, ransomware actors have been observed diversifying their data exfiltration tools. Symantec’s recent findings reveal a concerning trend where attackers are using a variety of tools for data exfiltration, including both malware and legitimate software with malicious intent. This evolution in tactics poses a significant challenge to cybersecurity professionals tasked with defending against ransomware attacks.
Cloud Threat Landscape
Cado Security’s release of the Cloud Threat Findings report for the second half of 2023 sheds light on the evolving cloud threat landscape. As organizations increasingly migrate their operations to the cloud, the risk of cloud-focused threat actors targeting sensitive data grows. The report provides valuable insights for security teams looking to bolster their defenses against cloud-based malware campaigns.
In conclusion, the cybersecurity landscape is constantly evolving, with threat actors becoming more sophisticated in their tactics. It is imperative for organizations and individuals alike to stay vigilant, keep their systems updated, and implement robust security measures to mitigate the risks posed by malicious actors.