The Linux Supply Chain Hack: A Narrow Escape
As I sit down to write this article, the recent discovery of a backdoor in the code of most Linux distributions still lingers in my mind. The news of the supply chain hack sent shockwaves through the tech community, but thanks to the swift action taken by Red Hat and other key players, disaster was averted.
The Discovery and Response
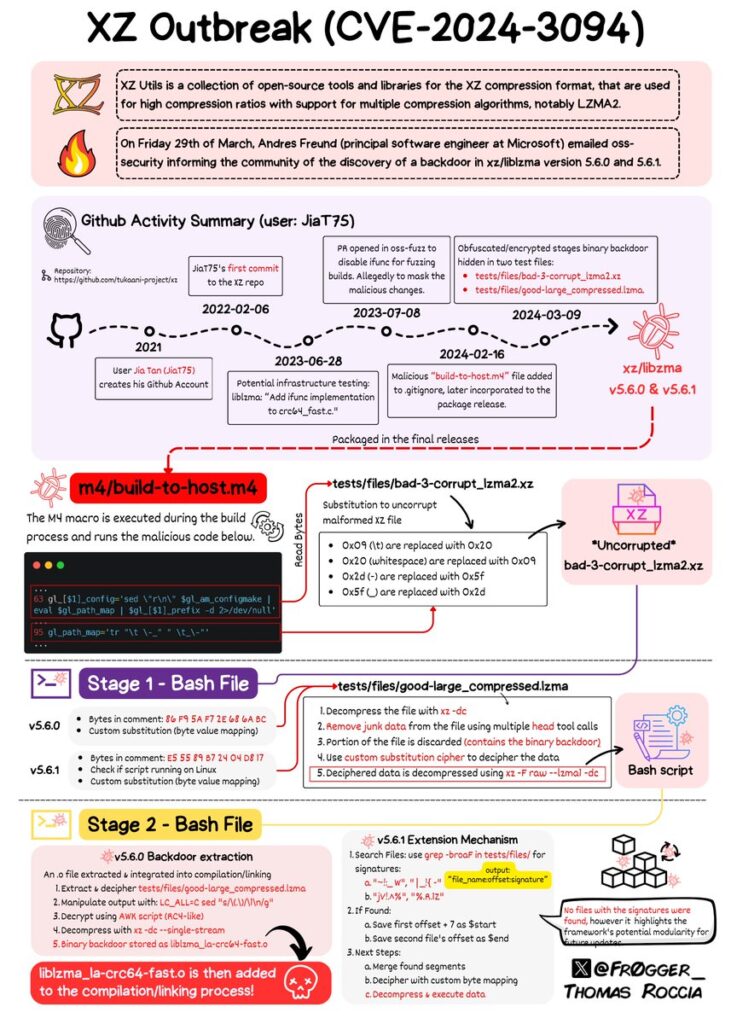
Vincent Danen, a prominent figure at Red Hat, played a crucial role in addressing the breach. The malicious code found its way into versions 5.6.0 and 5.6.1 of the XZ Utils libraries, a widely used set of data compression tools in Linux distributions. Red Hat, in collaboration with the U.S. Cybersecurity and Infrastructure Security Agency (CISA), wasted no time in alerting the community and taking steps to mitigate the threat.
A Collaborative Effort
Danen’s reassurance that the worst outcomes had been avoided brought a sense of relief. The joint efforts of Red Hat, CISA, and other Linux distributions underscored the importance of collaboration in the face of cybersecurity challenges. It was a testament to the resilience of the open-source community.
Uncovering the Vulnerability
The vulnerability was unearthed by Andres Freund, an engineer at Microsoft, who noticed unusual behavior in Debian installations. This keen observation led to the identification of the compromised versions of XZ Utils. While the affected versions were recent releases, the impact could have been far-reaching if left unchecked.
Immediate Actions
Users of the Fedora Rawhide distribution were promptly advised to halt usage and revert to a secure version. CISA’s recommendation to downgrade XZ Utils and conduct thorough checks for any signs of malicious activity highlighted the urgency of the situation. The vulnerability, tracked under CVE-2024-3094, served as a wake-up call for the entire Linux ecosystem.
In conclusion, the Linux supply chain hack serves as a stark reminder of the ever-present cybersecurity threats facing the tech industry. The coordinated response to this incident exemplifies the resilience and vigilance required to safeguard our digital infrastructure.


 Photo by
Photo by