Breaking News: Trojan Revival Sparks Panic Among Security Experts
In a shocking turn of events, a 20-year-old Trojan has made a comeback, sending ripples of concern through the cybersecurity community. The Trojan, known as Bifrost (aka Bifrose), has reemerged with a series of new variants specifically targeting Linux systems. Security researchers at Palo Alto Networks were the first to uncover this alarming development.
The latest Linux variant of the Bifrost malware employs a cunning tactic called typosquatting to masquerade as a legitimate VMware domain, thus evading detection mechanisms. This deceptive malware is designed to stealthily collect sensitive user data and transmit it back to a remote server, utilizing RC4 encryption to cloak its malicious activities.
The Rise of ARM-Based Malware
Adding to the complexity of the situation, there are indications that cybercriminals are broadening the scope of Bifrost’s reach by introducing a malicious IP address associated with a Linux variant hosting an ARM version of the malware. By offering an ARM-compatible iteration of the Trojan, hackers can infiltrate devices that were previously immune to traditional x86-based threats.
As the prevalence of ARM-based devices continues to grow, threat actors are adapting their strategies to include ARM-specific malware. This shift not only fortifies their offensive capabilities but also extends the potential targets of their attacks, posing a significant challenge to cybersecurity professionals.
Unveiling the Distribution and Infection Tactics
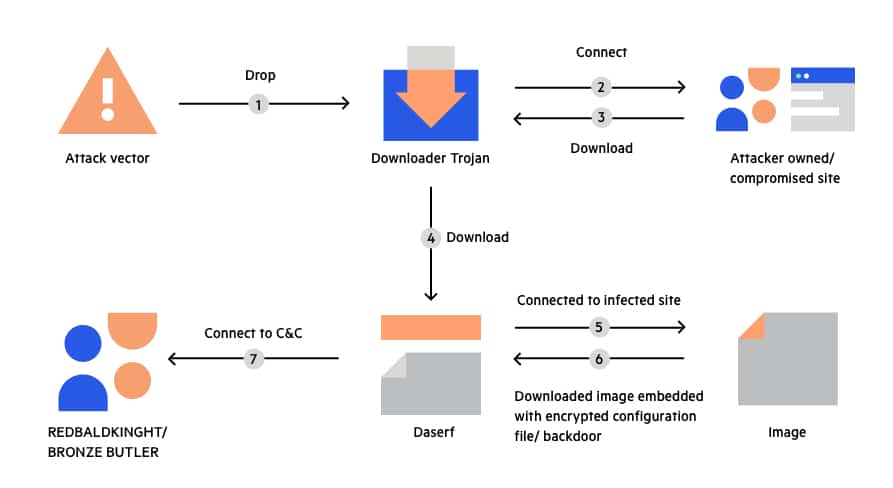
The distribution channels for Bifrost are as varied as they are insidious. Attackers commonly disseminate the malware through email attachments or compromised websites. Recent findings by Palo Alto researchers uncovered a sample of Bifrost hosted on a server linked to the domain 45.91.82[.]127. Once implanted on a victim’s system, Bifrost establishes communication with a command-and-control (C2) domain cleverly named download.vmfare[.]com, a deceptive clone of the legitimate VMware domain.
Protecting Sensitive Data in the Digital Age
Despite its age, the Bifrost Remote Access Trojan (RAT) remains a potent and evolving menace to both individuals and organizations. The adoption of typosquatting by new Bifrost variants underscores the importance of proactive malware detection and mitigation strategies. Vigilance in tracking and neutralizing threats like Bifrost is paramount to safeguarding confidential information and upholding the security of computer networks.
 Image for illustrative purposes
Image for illustrative purposes