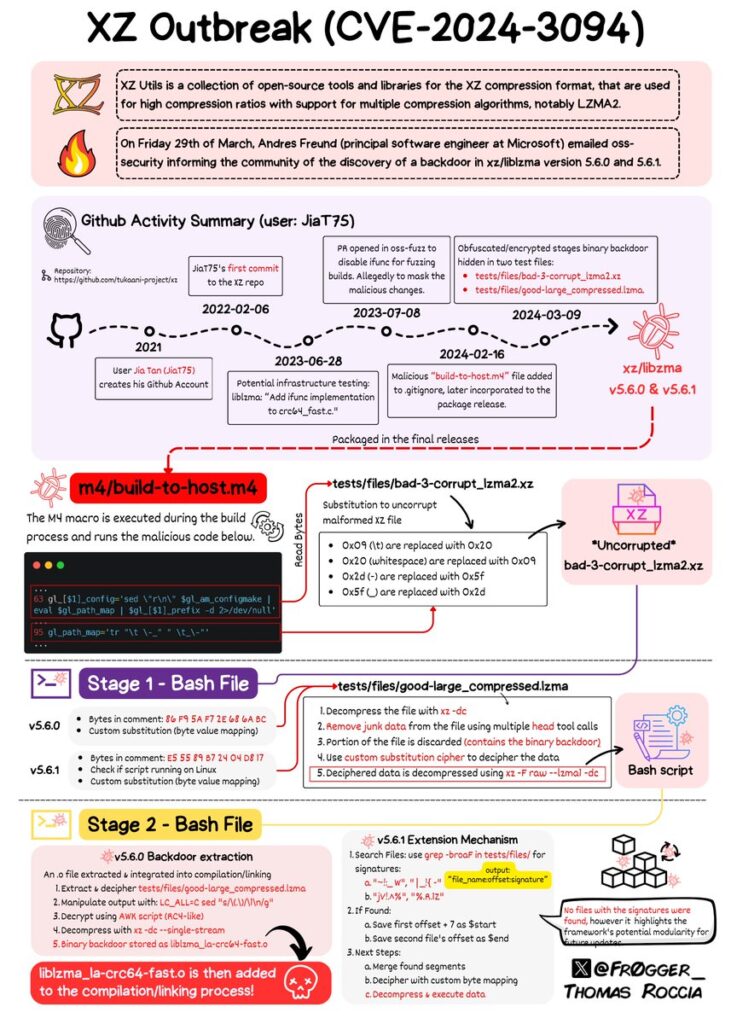
The Hidden Dangers of Linux: Unveiling the Truth Behind the XZ Utils Backdoor
As a seasoned tech journalist, I’ve always prided myself on uncovering the lesser-known aspects of the digital world. Today, I delve into the recent revelation that has sent shockwaves through the Linux community: the malicious backdoor code lurking within the widely-used XZ Utils tool.
A Deceptive Facade
The software giant Red Hat and the cybersecurity stalwart CISA have sounded the alarm on a covert threat embedded within XZ Utils, a seemingly innocuous tool designed to streamline file compression. This insidious backdoor, identified as CVE-2024-3094, poses a grave risk to the integrity of Linux distributions, with Red Hat cautioning that the vulnerability extends far and wide across the ecosystem.
Unraveling the Conspiracy
In a move reminiscent of a cyber espionage thriller, reports indicate that versions 5.6.0 and 5.6.1 of XZ Utils have been compromised, potentially granting unauthorized access to malevolent actors. The implications are dire, with the Cybersecurity and Infrastructure Security Agency urging swift action to mitigate the threat. Developers and users are advised to downgrade to the secure XZ Utils 5.4.6 Stable release, a temporary solution to a problem that runs deep.
The Race Against Time
Amid the chaos, the tech community finds itself in a race against time to identify the perpetrators behind this sophisticated attack. Microsoft engineer Andres Freund’s discovery sheds light on the shadowy origins of the backdoor, with experts tracing its roots back to March 26. The implications are far-reaching, signaling a concerted effort to infiltrate open-source supply chains and compromise the very foundation of digital security.
Navigating the Fallout
As organizations grapple with the fallout of this breach, cybersecurity luminary John Bambenek underscores the urgency of the situation. The compromised library, a staple in modern Linux distributions, underscores the pervasive nature of the threat. The call to action is clear: prioritize security, even if the tools at risk aren’t part of your daily toolkit.
A Call to Vigilance
In the wake of this revelation, the onus falls on Linux users to exercise vigilance and diligence in safeguarding their systems. The specter of unauthorized access looms large, underscoring the critical need for proactive measures to fortify digital defenses.
Embracing Resilience
While the XZ Utils debacle serves as a stark reminder of the vulnerabilities that permeate the digital landscape, it also underscores the resilience and adaptability of the tech community. By banding together in the face of adversity, we can emerge stronger and more secure than ever before.















