New Critical Vulnerability Discovered in GNU C Library’s Dynamic Loader
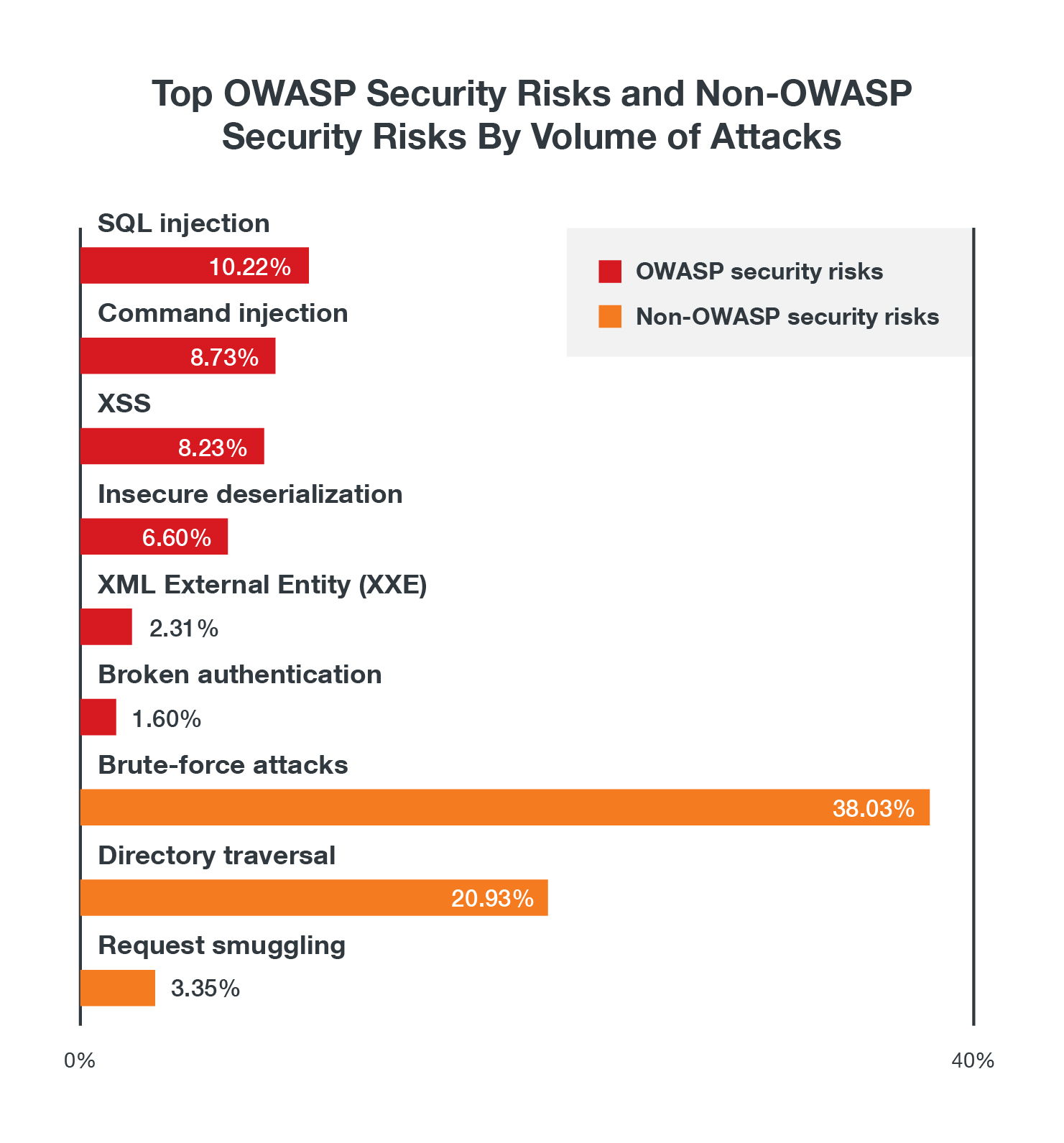
Security researchers at Qualys Threat Research Unit (TRU) have unearthed a significant security flaw within the GNU C Library’s dynamic loader. The vulnerability, linked to the processing of the GLIBC_TUNABLES environment variable, poses a grave threat to the security of popular Linux distributions.
To exploit this vulnerability, attackers could potentially gain root privileges, opening the door to unauthorized data access, alteration, or deletion. This breach could further escalate into more severe attacks by leveraging escalated privileges.
The research team’s investigation revealed that the vulnerability affects default installations of well-known Linux distributions, including Fedora 37 and 38, Ubuntu 22.04 and 23.04, and Debian 12 and 13. While the initial introduction of the vulnerability dates back to April 2021, other distributions are also at risk of exploitation.
The dynamic loader of the GNU C Library plays a critical role in the preparation and execution of programs, making it a prime target for malicious actors. A successful exploit could have far-reaching consequences, impacting system performance, reliability, and overall security.
Vulnerability Impact on IoT Devices
One of the most vulnerable sectors to this glibc vulnerability is the realm of IoT (Internet of Things) devices. These devices heavily rely on the Linux kernel within their custom operating systems, rendering them susceptible to potential security breaches.
The Qualys TRU promptly notified Linux package maintainers about the issue on September 4 and provided a patch on September 19th. Security teams are strongly advised to prioritize the application of this patch to mitigate the inherent risks posed to Linux distributions.
Security Vulnerability