As a journalist covering cybersecurity, I often come across alarming news about vulnerabilities that could potentially compromise our systems. Recently, a critical vulnerability in the shim bootloader caught my attention. The maintainers at RedHat have successfully patched this vulnerability, which could have allowed attackers to gain privileged access to a Linux system even before the kernel was loaded. This revelation sent shockwaves through the cybersecurity community, as it posed a significant threat to the security of Linux systems supporting the Secure Boot process.
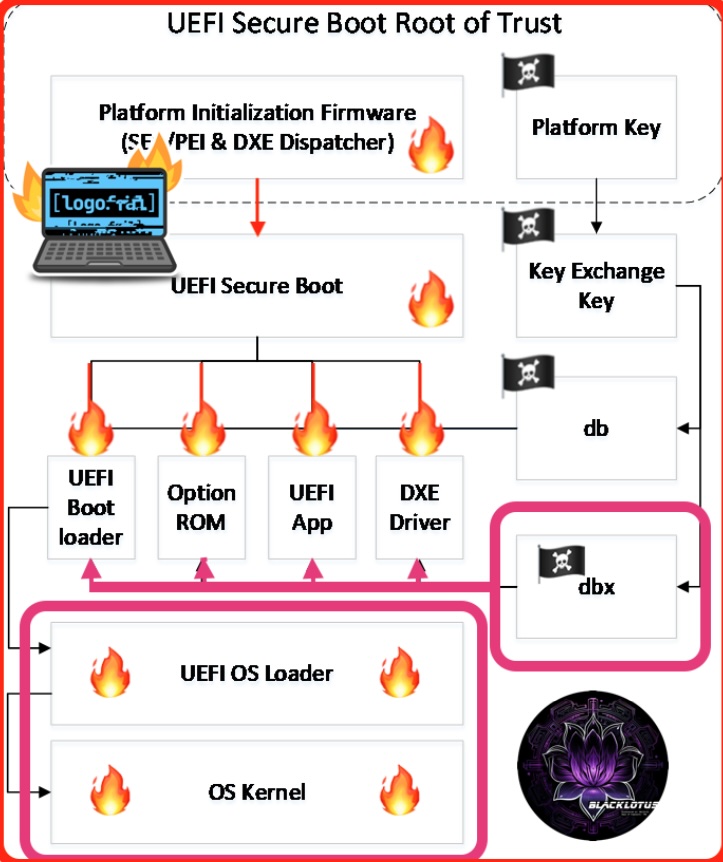
The vulnerability, identified as CVE-2023-40547, raised serious concerns among security professionals due to its ability to grant attackers pre-operating system control, effectively bypassing the security measures enforced by Secure Boot. The implications of such a flaw are dire, as attackers could exploit various attack paths to disrupt or take control of the entire boot process, potentially leading to a complete system takeover.
While the initial focus may have been on RedHat systems, it’s essential to note that the bug impacts all Linux systems utilizing Secure Boot, including servers and end-user systems. The gravity of the situation prompted other major Linux distributions like Debian, Ubuntu, and SUSE to swiftly apply the necessary patches to address the vulnerability.
In addition to the critical vulnerability, five other medium-severity flaws were discovered in shim, further underscoring the importance of proactive cybersecurity measures. Given the widespread use of Linux in business environments, the urgency of patching this issue cannot be overstated.
One expert, John Gallagher, the vice president of Viakoo Labs, highlighted the severity of the threat posed by this vulnerability. Gallagher emphasized how threat actors target the weakest links in an organization’s defenses, exploiting vulnerabilities that are challenging to remediate quickly. The shim vulnerability aligns perfectly with this modus operandi, presenting an exploitable weakness across a broad spectrum of devices and system types.
The unique challenge posed by the shim vulnerability lies in its early-stage presence in the system’s software and hardware interactions. This early initialization stage grants root access to various services, significantly expanding the attack surface for potential malicious actors. The pervasiveness of Linux in non-IT systems like IoT and OT further complicates the mitigation and remediation efforts, as these systems lack the layered security defenses typically found in traditional IT environments.
Unlike conventional IT setups with multiple security layers, IoT and OT systems running Linux remain vulnerable to the shim exploit, potentially remaining infected and undetected. Organizations with extensive IoT/OT deployments must prioritize implementing application-based IoT discovery and automated remediation solutions for firmware updates to mitigate the risks posed by this vulnerability.
Linux administrators are strongly advised to expedite the patching process by updating to the latest shim version promptly. Failing to address this vulnerability promptly could have severe consequences, allowing threat actors to bypass endpoint protections and install a bootkit, granting them elevated privileges and potentially full control over the system. The insidious nature of this exploit, occurring at such a low level in the system and early in the boot process, makes detection challenging by conventional means, leaving systems vulnerable until it’s too late.